HTB Getting Started Module – Knowledge Check
Academy Walkthrough, HTBInitial nmap scan of the target
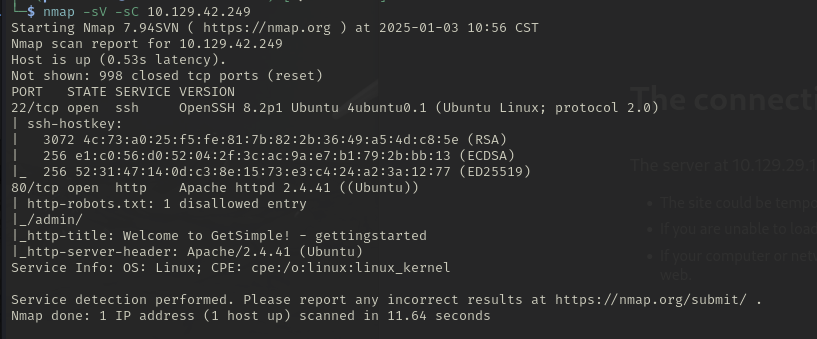
We find there is a website being hosted, and it is a blog using the GetSimple! CMS. Nmap also shows us there is a robots.txt file. From the robots.txt page we find there is an admin page:

Navigating to the login page and a simple test of admin:admin gains us access to the admin portal:

After looking around in the admin portal, we find there is a web page editor where we can edit a themes PHP code:
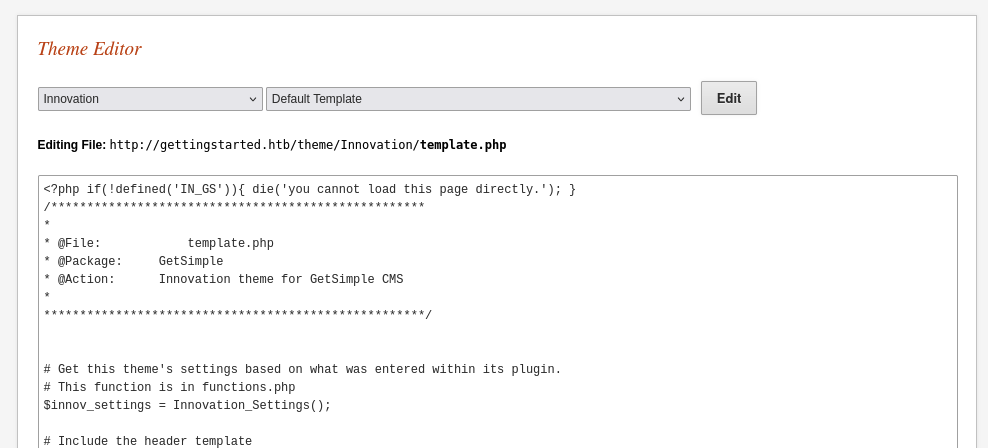
If we try to navigate to the template.php webpage we see we are given the message “you cannot load this page directly.” (which is the first line of PHP code in the file) Removing this line of code and replacing it with a reverse shell one liner will do the trick with a netcat listener ready.

Now we navigate to the template page, and we are given a reverse shell.

Now we can navigate to users home directory and get the user.txt flag. After running the sudo -l command, we can see what privileged commands we can run without a password:

From here, we simply execute a php script on the command line to give us another reverse shell:

On our netcat listener, we are given the # root user and able to navigate and grab the root.txt flag.
